
Be Prepared – Cyber Blackout
“If I could give someone just one life tip, I’d tell them to be prepared. I can’t think of better words to live by that

“If I could give someone just one life tip, I’d tell them to be prepared. I can’t think of better words to live by that

“Wickr has built a sophisticated end-to-end encryption protocol that provides their users with strong cryptographic guarantees.” – Dr. Matthew Green, Cryptographer & Professor at Johns

Can secure communication tools and a renewed focus on information governance systems help legal professionals and IT departments combat an increasingly pervasive threat vector? How

“Everyone has to assume that content shared via business email and traditional collaboration platforms is not protected. Enabling quick adoption of secure communications tools with

Does your workday start when you actually sit at your desk and turn on your PC? For most workers, the start of your workday isn’t
* The content of this paper was presented at 2017 AppSecUSA In an age of ever more sophisticated cybercrime and mass surveillance, secure communication is
The Wickr platform is built around two types of secrets: cryptographic keys and passwords. This paper is focused on passwords. First, I’ll explain why Wickr
“The messages are encrypted end-to-end and both the encrypted messages and keys in the key pools are authenticated end-to-end. This means that attackers have no

Wickr Enterprise is engineered to meet any record retention, auditing, and data security requirements for regulated industries. It is specifically designed to enable organizations to enforce transparency and accountability in compliance with statutory data retention standards (i.e. FINRA, PRA, FRA, FOIA) while ensuring maximum security of high-target communications.

We are excited to release a new feature enabling screenshot detection on Android and iOS for both AWS Wickr and Wickr Me. While there is
With so much happening in the news, it is increasingly harder for consumer – whether businesses or end users – to trust technologies we all
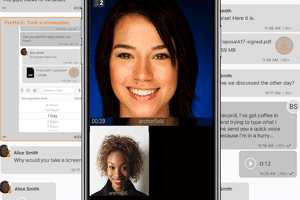
Since we added calling to AWS Wickr, teams have enjoyed end-to-end encrypted conferencing across the office or with partners across the world. From executives to

It seems every new app or online service these days is designed to entice you to share your activity, location, or personal information at all

Trust is the pivotal building block of the attorney-client relationship. This critical relationship requires the exchange and divulgence of confidential or privileged information— from trade

Last week, a security-related flaw in Electron, a popular software framework, hit the news. This was particularly painful as Electron, an application development framework that

Imagine a team detecting the signs of a data breach within a global network, or a multinational company launching a new product in a hostile new market.

Traditional methods of protecting valuable business and personal data are an arms race with no winners. It is time for a new strategy & platforms that enable data minimization and ensure that service providers & adversaries are kept out.